
The Texas State Bar was breached in early 2025 and all their sensitive data was exfiltrated, before they even knew they were hacked. The culprits? The INC Ransomware group, notorious for their digital extortion. This headline is a cautionary warning to all lawyers, not just Texas lawyers. One breach could have lasting consequences for client trust, firm reputation, and business continuity.
Ransomware attacks like this are becoming more common, and there is a lot to learn from the Texas Bar cyberattack. How did it happen? How does INC Ransomware operate? Why did it take so long to figure out they had been hacked?
Pro-Tip: Read the 3 Steps to Protect Your Law Firm
Understanding the Texas Bar Hack
The digital alarm bells rang silently within the State Bar's systems. The initial detection of the intrusion marked the beginning of this cybersecurity nightmare. The State Bar determined that there was unauthorized access to their data between January 28 and February 9, 2025. They detected the attack on February 12.
In March, INC Ransomware claimed responsibility for the attack. Ransomware is a particularly insidious form of cybercrime where malicious software encrypts data, rendering it inaccessible until a ransom is paid. The data is often exfiltrated, allowing for a second round of ransom demands. Corrupting backups is also a common tactic, making it much harder to dodge paying the ransom.
While specific systems and the exact types of data compromised remain largely under wraps in public disclosures, the potential implications for the Texas Bar and its members are significant, given the sensitive nature of legal information.
What’s the Impact?
What makes this breach particularly concerning is the nature of the compromised data. Legal documents and personally identifiable information are incredibly sensitive. Their exposure can have far-reaching consequences, potentially undermining ongoing litigation, compromising individual privacy, and opening the door to various forms of fraud and identity theft.
This incident at the State Bar of Texas serves as a crucial wake-up call, not just for legal organizations, but for any entity handling sensitive data. Relying on outdated security protocols or failing to invest adequately in cybersecurity infrastructure is no longer an option.
Here's what you can do to protect your sensitive information:
- Change passwords regularly and enable Multi-Factor Authentication.
- Be wary of phishing attempts and scams.
- Ensure that your devices are running up-to-date software.
- Upgrade your cybersecurity, investigate tools like NetSafe®MDR or immutable backups.
- Have a Business Continuity plan.
By taking these proactive steps, firms can significantly reduce their vulnerability and minimize the potential repercussions of a data breach.

How does INC Ransomware operate?
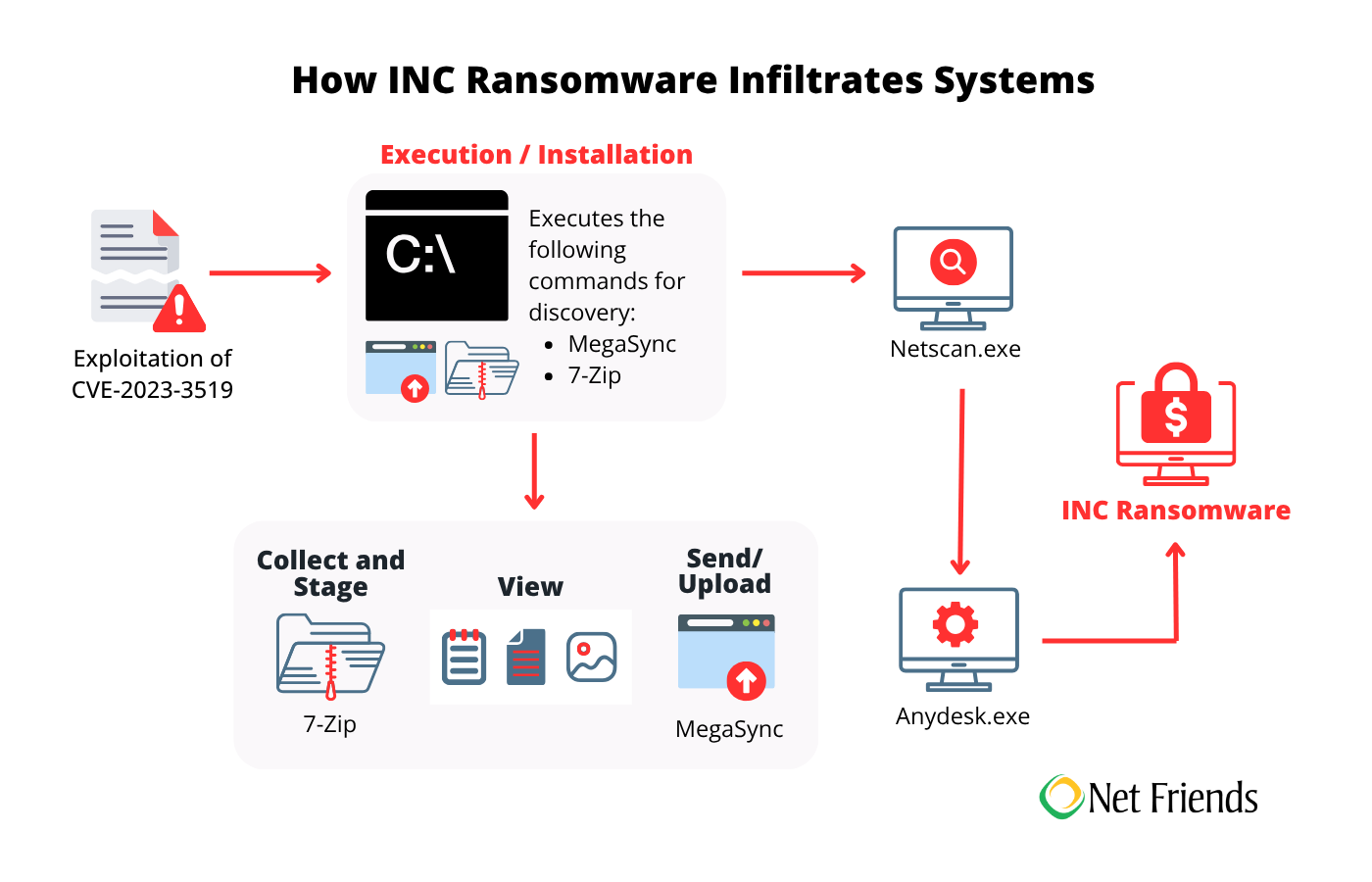
The INC Ransom gang, responsible for the breach at the State Bar of Texas, employs a sophisticated and multi-stage approach to execute their ransomware attacks. Their modus operandi goes beyond simple encryption; it often involves a "double extortion" strategy, designed to maximize pressure on their victims.
The attack typically begins with initial access. This can be achieved through various vectors, including:
- Exploiting unpatched vulnerabilities: By finding and exploiting these unaddressed flaws, they can gain a foothold within an organization's network.
- Spear-phishing: This involves highly targeted email campaigns designed to trick employees into clicking malicious links or opening infected attachments.
- Purchased valid account credentials: In some cases, INC Ransomware may acquire legitimate user credentials from initial access brokers on the dark web, allowing them to log in directly to a network.
Once initial access is gained, the threat actors focus on privilege escalation and lateral movement. They do not just stay in one place, they aim to spread throughout the network, gaining higher levels of access. This involves:
- Network reconnaissance: They scan the network to map out its architecture, identify critical systems, and locate valuable data.
- Credential access: They deploy tools that will allow them to gain access to more accounts, including those with administrative privileges.
- Lateral movement tools: They leverage legitimate remote access software such as AnyDesk to move from one compromised machine to another, expanding their control over the network.
- Disabling security features: To avoid detection and hinder recovery, INC Ransomware may attempt to disable antivirus software and other security features.
Before deploying the ransomware, the INC Ransomware gang often engages in data exfiltration. This is a key component of their "double extortion" strategy. They identify and steal sensitive data, such as personally identifiable information (PII), financial records, and intellectual property.
Finally, the encryption and extortion phase begins. They may employ different encryption modes, including "fast" or "medium" encryption, which encrypts portions of files to accelerate the process while still rendering the data unusable.
To further impede recovery, the ransomware attempts to delete Volume Shadow Copies and other backup files. Once this is all complete, they send the ransomware notifications.
In essence, the INC Ransomware gang combines initial infiltration with extensive network reconnaissance, privilege escalation, data theft, and targeted encryption, all orchestrated to maximize their financial gain and pressure victims into capitulation.
Protecting Your Firm
The INC Ransom gang's successful infiltration of the State Bar's network is a reminder that no organization is immune to these sophisticated attacks. As we navigate an increasingly interconnected world, the onus is on organizations to prioritize cybersecurity as a fundamental aspect of their operations, not just an afterthought. One breach can destabilize a firm by compromising client trust and undermining the firm's reputation.
Net Friends uses a wide range of strategies to help their clients protect their sensitive data. If you would like to learn more about how we can help you, book a meeting with one of our IT Experts.
Follow us on LinkedIn.
More Reading:
3 Steps to Protect Your Law Firm
NetSafe® MDR Protects Your Business System
Why Law Firms Should Secure Their Inboxes
Take IT Off Your To-Do List.
Tech holding you back? Losing productivity to downtime?
Discover how we can simplify your tech and free up your time, contact us today.
At Net Friends, we believe in the power of human expertise. While we leverage AI to enhance our content and processes, all blog posts are written and edited by our knowledgeable staff. You can trust you are getting insights directly from our team.

