Your Essential Guide to Implementing SPF, DKIM, and DMARC
In today’s digital landscape, email remains the most critical business communication tool, and the favored entry point for cyber attackers. With the average office worker managing over 120 emails daily, the risk of a single mistake compromising your organization is higher than ever.
Email serves as the central, high-traffic hub of the modern digital business; like Grand Central Station where messages arrive and depart. While email’s universal accessibility makes it a vital communication tool, its inherent openness is also the primary vulnerability exploited by cyber attackers. Because core email protocols are fixed and designed for maximum access, fortifying your inbox requires proactive security enhancements. Implementing these measures is essential to transform this public communication channel into a trusted and protected resource.
Why Email is the Top Cyber Attack Vector
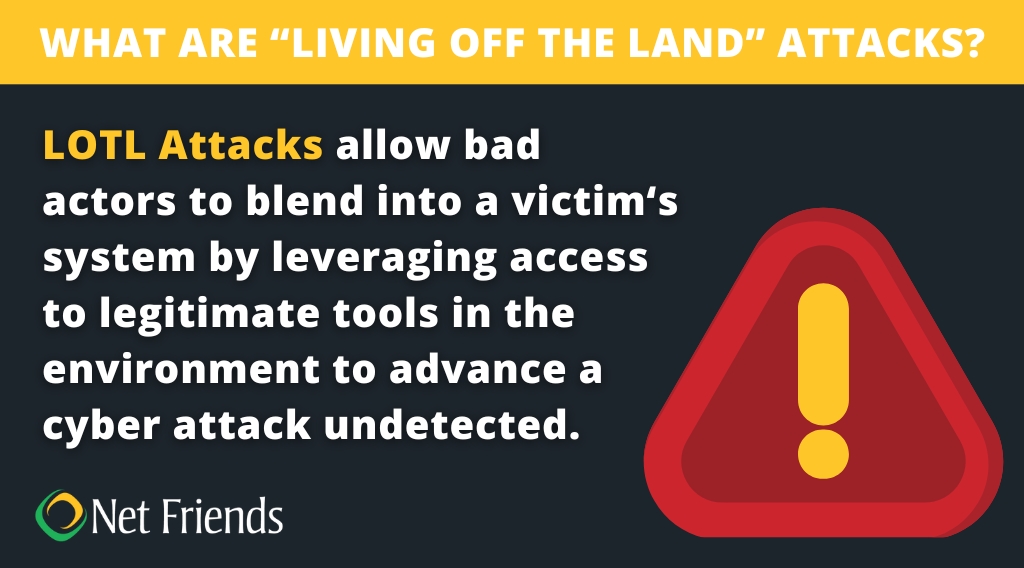
Modern hackers are moving away from easily detected viruses and malware, prioritizing attacks that exploit human error and compromised credentials. According to Huntress, a third of recent cyberattacks were code-free. These living off the land strategies breach defenses through legitimate channels, often starting with a single compromised email account, and slipping past traditional security measures designed to detect malicious code.
Living Off the Land (LOTL) Attacks: Hackers often initiate these attacks by tricking employees into giving up login credentials (phishing). They then use these legitimate accounts to perform "code-free" actions, like deleting files or conducting fraudulent transactions. This strategy bypasses traditional security measures designed to detect malicious software.
Fortifying Your Domain
To secure your business email against spoofing and phishing, you must implement three foundational email authentication protocols. These settings act as a master control center for your email domain, signaling trust to recipients worldwide.
Why DMARC is Now Non-Negotiable
Despite their importance, very few businesses have taken these steps. Only a mere 14% of companies have DMARC properly configured. This leaves a significant gap in the global fight against spam and phishing attacks.
Email Provider Requirements: Major service providers like Google (Gmail) and Yahoo are beginning to require senders, especially bulk senders, to have DMARC properly configured to ensure reliable email delivery.
Without these essential records, your business emails are increasingly likely to be automatically rejected, bounced, or classified as spam by recipient servers, regardless of the content.
Implementing DMARC establishes a standard of trustworthiness for your domain, allowing receiving systems globally to confidently reject fraudulent messages claiming to be from your organization.
What Can Your Business Do?
While setting up SPF, DKIM, and DMARC requires attention to technical detail, the long-term benefits outweigh the initial effort.
- Check Your Configuration: Use online tools to verify if your domain currently has valid SPF, DKIM, and DMARC DNS records published.
- Consult Your IT Partner: Reach out to your Managed Service Provider (MSP) or IT team for expert guidance. These records must be crafted meticulously to ensure legitimate email delivery is not interrupted.
- Adopt a Policy: A secure domain is a trusted domain. By implementing the SPF, DKIM, and DMARC security trifecta, you fortify your business's digital identity and contribute to a safer internet ecosystem.
If a concerted effort were made to encourage the widespread implementation of SPF, DKIM, and DMARC, especially among small and medium-sized businesses (SMBs), the collective security against fraudulent emails would be greatly improved. It would enable a global standard, allowing us to confidently reject messages from unverified senders and more effectively blacklist malicious sources.
Unsure where to start? Net Friends can help you navigate the complexities of implementing SPF, DKIM, and DMARC.
Follow Us on LinkedIn.
More Reading:
- 5 Tips to Improve Your Cybersecurity Culture
- Top 7 Questions to Ask a Cybersecurity Provider
- Top 10 Basic Security Trainings to Build Your Cybersecurity Culture
Take IT Off Your To-Do List.
Tech holding you back? Losing productivity to downtime?
Discover how we can simplify your tech and free up your time, contact us today.
At Net Friends, we believe in the power of human expertise. While we leverage AI to enhance our content and processes, all blog posts are written and edited by our knowledgeable staff. You can trust you are getting insights directly from our team.

